Ssh Key Generation Using Git
Generating a new SSH key Open the terminal. Paste the text below, substituting in your GitHub email address. When you're prompted to 'Enter a file in which to save the key,' press Enter. At the prompt, type a secure passphrase. For more information.
- Git Which Ssh Key
- How To Generate Ssh Key Using Git Bash
- Git Ssh Key Generation
- Ssh Key Generation Command In Git
- Ssh Key Generation Using Git Key
Azure Repos Azure DevOps Server 2019 TFS 2018 TFS 2017 TFS 2015 Update 3
Jul 25, 2019 Execute the following command: ssh-keygen -t rsa (when prompted, enter password, key name can stay the same) Open the file you’ve just created /.ssh/idrsa.pub with your favorite text editor, and copy contents to your Git repository’s keys field (GitHub, beanstalk, or any other repository provider), under your account. There are several authentication methods into a VM, including an SSH public/private key pair or a username and password. We strongly recommend using key-based authentication (if you use a username/password, you'll be prompted to enter your credentials more than once by the extension). SSH keys are a way to identify trusted computers, without involving passwords. The steps below will walk you through generating an SSH key and adding the public key to the server. Step 1: Check for SSH Keys First, check for existing SSH keys on your computer. Open Git Bash, Cygwin, or Terminal, etc. Generating an SSH Key on Windows - using Git: Download Git, run the Git.exe file and install the app. When you get to the “Adjusting your PATH variable environment” screen, choose Use Git Bash only. Next, on the “Configuring the line ending conversions” screen, choose Checkout as-is, commit as-is. Then proceed with the installation.
Choose a method to securely access the code in Azure Repos, Azure DevOps Server 2019, or Team Foundation Server (TFS) Git repositories.Use these credentials with Git at a command prompt. These credentials also work with any Git client that supports HTTPS or SSH authentication.Limit the scope of access and revoke these credentials when they're no longer needed.
Important
Azure DevOps no longer supports Alternate Credentials authentication since the beginning of March 2, 2020. If you're still using Alternate Credentials, then they won't work anymore. You have to switch to a more secure authentication method, to mitigate this breaking change impacting your DevOps workflows. Learn more.
Azure DevOps Server was formerly named Visual Studio Team Foundation Server.
Tip
Using Visual Studio? Team Explorer handles authentication with Azure Repos for you.
Authentication comparison
| Authentication Type | When to use | Secure? | Ease of setup | Additional tools |
|---|---|---|---|---|
| Personal access tokens | You need an easy to configure credential or need configurable access controls | Very secure (when using HTTPS) | Easy | Optional (Git credential managers) |
| SSH | You already have SSH keys set up, or are on macOS or Linux | Very secure | Intermediate | Windows users will need the SSH tools included with Git for Windows |
| Alternate credentials | You can't use personal access tokens or SSH | Least secure | Easy | See important information about alternate credentials |
Personal access tokens
Personal access tokens (PATs) give you access to Azure DevOps and Team Foundation Server (TFS), without using your username and password directly.These tokens have an expiration date from when they're created. You can restrict the scope of the data they can access.Use PATs to authenticate if you don't already have SSH keys set up on your system or if you need to restrict the permissions that are granted by the credential.
Use Git Credential Manager to generate tokens
/bioshock-infinite-steam-cd-key-generator.html. Git credential managers is an optional tool that makes it easy to create PATs when you're working with Azure Repos.Sign in to the web portal, generate a token, and then use the token as your password when you're connecting to Azure Repos.
PATs are generated on demand when you have the credential manager installed.The credential manager creates the token in Azure DevOps and saves it locally for use with the Git command line or other client.
Note
Current versions of Git for Windows include the Git credential manager as an optional feature during installation.
SSH key authentication
Key authentication with SSH works through a public and private key pair that you create on your computer.You associate the public key with your username from the web. Azure DevOps will encrypt the data sent to you with that key when you work with Git.You decrypt the data on your computer with the private key, which is never shared or sent over the network.
SSH is a great option if you've already got it set up on your system—just add a public key to Azure DevOps and clone your repos using SSH.If you don't have SSH set up on your computer, you should use PATs and HTTPS instead - it's secure and easier to set up.
Learn more about setting up SSH with Azure DevOps
Alternate credentials
Create an alternate user name and password to access your Git repository using alternate credentials.Unlike PATs, this login doesn't expire and can't be scoped to limit access to your Azure DevOps Services data.Use alternate credentials as a last resort when you can't use PATs or SSH keys.
SSH keys are a way to identify trusted computers, without involving passwords. The steps below will walk you through generating an SSH key and adding the public key to the server.
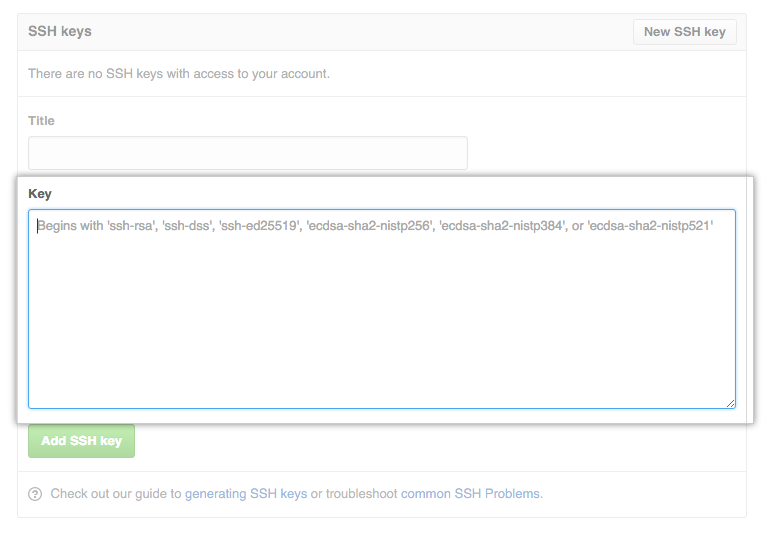
Step 1: Check for SSH Keys
First, check for existing SSH keys on your computer. Open Git Bash, Cygwin, or Terminal, etc. and enter:
Git Which Ssh Key
Check the directory listing to see if you already have a public SSH key. By default, the filenames of the public keys are one of the following: Qemu download mac os x.
- id_dsa.pub
- is_ecdsa.pub
- id_ed25519.pub
- id_rsa.pub
If you see an existing public and private key pair listed (for example id_rsa.pub and id_rsa) that you’d like to use, you can skip Step 2 and go straight to Step 3.
Step 2: Generate a new SSH key
With your command line tool still open, enter the text shown below. Make sure you substitute in your email address:
You’ll be asked to enter a passphrase, or simply press Enter to not enter a passphrase:
After you enter a passphrase (or just press Enter twice), review the fingerprint, or ‘id’ of your SSH key:

Step 3: Add your key to the ssh-agent
To configure the ssh-agent program to use your SSH key, first ensure ssh-agent is enabled.
If you are using Git Bash, turn on the ssh-agent with command shown below instead:
Then, add your SSH key to the ssh-agent:
How To Generate Ssh Key Using Git Bash
Step 4: Add your SSH key to the server
Git Ssh Key Generation
To add your public SSH key to the server, you’ll copy the public SSH key you just created to the server. Substitute “username” with your username on the server, and “server.address.com” with the domain address or IP address of your server:
Ssh Key Generation Command In Git
The server will then prompt you for your password:
Ssh Key Generation Using Git Key
That’s it! You should now be set up to connect to the server without having to authenticate.